SharpProcessDump - Dump processes using C#
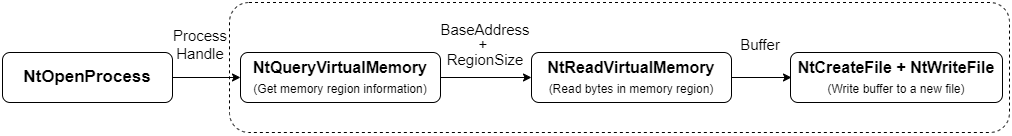
Dump memory regions of a process which are readable (no PAGE_NOACCESS protection) and are commited (MEM_COMMIT state) using only native API calls.
The native API calls used are: : NtOpenProcess, NtQueryVirtualMemory, NtReadVirtualMemory, NtCreateFile and NtWriteFile.
Repository: https://github.com/ricardojoserf/SharpProcessDump
Usage
It generates one file per memory region and one file containing all the memory chunks.
SharpProcessDump.exe [PROCESS] [FILE]
The default value for the process is “lsass” and for the file containing all memory chunks it is “Process_PID_allinone.dmp”.
Example: Dumping lsass
SharpProcessDump.exe lsass lsass_allinone.dmp
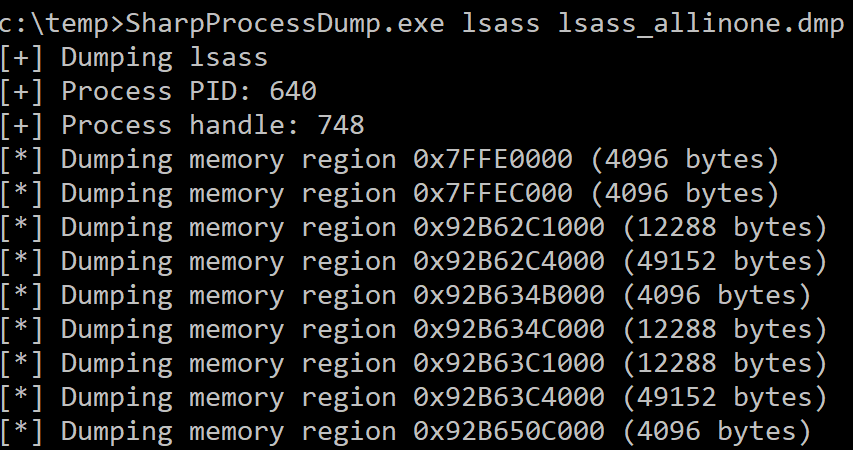
It generates one file per memory region using the process name, PID and memory address for the name (the syntax is “Process_PID_MEMADDRESS.dmp”) and the file “lsass_allinone.dmp” containing all the memory chunks:
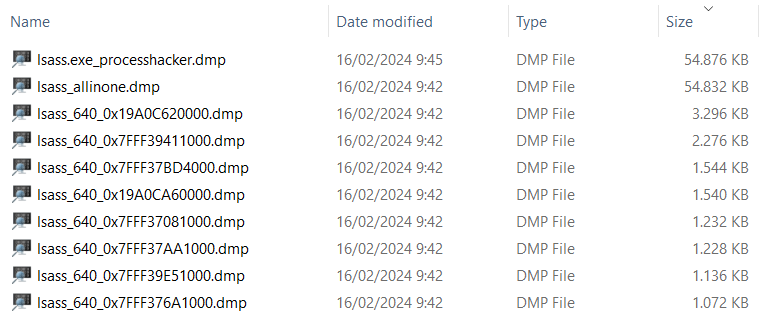
As you can see in the image above, the size between the dump file created using Process Hacker and this tool have almost the same size.