NativeNtdllRemap - Stealthy ntdll.dll Remapping
Use only NTAPI functions to stealthily remap ntdll.dll from a clean .text section of a suspended process. This technique bypasses user-mode API monitoring and enhances evasion against security solutions.
Repository: https://github.com/ricardojoserf/NativeNtdllRemap
The NTAPI functions used by the tool are:
-
NtCreateUserProcess: Create a process in suspended state
-
NtProtectVirtualMemory: Change memory protection
-
NtQueryInformationProcess: Retrieve process information
-
NtReadVirtualMemory: Read memory content
-
NtClose and NtTerminateProcess: Close object handles and processes
-
RtlCreateProcessParametersEx and RtlDestroyProcessParameters: Manage Process Parameters
-
RtlAllocateHeap and RtlFreeHeap: Manage heap memory
-
RtlInitUnicodeString and RtlUnicodeStringToAnsiString: Manage strings
The program creates the suspended process, calculates the addresses and waits for a key to be pressed:
Using System Informer (formerly known as Process Hacker), it is possible to check the initial content of the ntdll.dll’s “.text” region in the current process:
Change the memory contents and click “Write”:
Press any key so the memory is overwritten:
Click “Re-read” to find the “.text” section has been replaced with the content of the suspended process’ “.text” section:
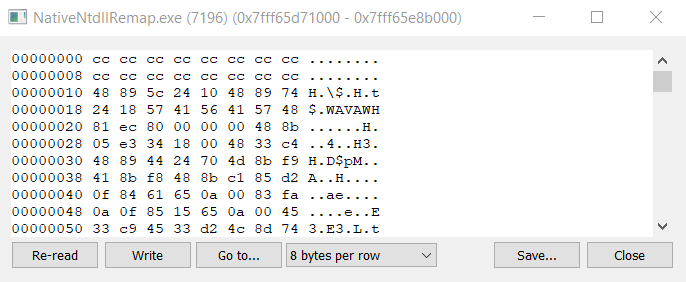
Finally, press any key so the “.text” section protections are restored and the program finishes:
NOTE: Comment lines 451 and 453 in the ReplaceNtdllTxtSection function to prevent the program from pausing until a key is pressed.